- in Чӣ тавр ба by Admin
Бо истифода аз CMD чӣ гуна ҳамлаи DDoS-ро дар вебсайт анҷом додан мумкин аст

Today, it is very easy for a hacker to hack a website that is not secured. Even a single loophole in the website or application makes it easy for the hacker to hack it using different methods. And a DDoS attack is one of the widely used methods for the same. Using a DDoS attack, any small website can be crashed very easily. So, let us understand it more deeply.

Бо истифода аз CMD чӣ гуна ҳамлаи DDoS-ро дар вебсайт анҷом додан мумкин аст
Before learning how to perform a DDoS attack you must understand what is a DDoS attack.
Ҳамлаи DDoS чист?
DDoS stands for “Dтақсим карда шудааст Dнафратовар of Service”. A DDoS attack is a ҳамлаи киберӣ in which a perpetrator seeks to make a website, network, or a machine unavailable to its intended user(s) by temporarily disrupting the services of the host connected to the internet. Such attacks are usually carried out by hitting the target resource such as web servers, networks, emails, etc. with too many requests at the same time. Due to this, the server fails to respond to all the requests at the same time and leads to its crashing or slow down.
How Distributed Denial of Service (DDoS) attack works?
Every server has a predefined capacity of handling requests at a time and it can handle only that number of requests at that time. In order to implement a DDoS attack on a server, a large number of requests are sent at a single time to the server. Due to this, the data transmission between the server and the user disconnects. As a result, the website crashes or goes down temporarily as it loses its allotted bandwidth.
How to prevent a DDoS attack?
A DDoS attack can be prevented by:
- насби часбҳои амниятӣ.
- бо истифода аз системаҳои ошкоркунии ҳамла to identify and even stop any sort of illegal activities.
- Using a Firewall to block all the traffic coming from an attacker by identifying its IP.
- Or by using a router configured via the access control list (ACL) to limit the access to the network and drop the suspected illegal traffic.
Ҳамчунин хонед: Fix Sea of Thieves Services Are Temporarily Unavailable Lavenderbeard
Tools for performing a DDoS attack
The following are the tools commonly used for performing a DDoS attack.
1. Nemesy
It is used to generate random packets. It works on windows. Due to the nature of the program, if you have an antivirus, it will most likely be detected as a virus.
2. Land and LaTierra
This tool is used for IP spoofing and opening the TCP алоқаҳо.
3. Пантера
This tool can be used to flood a victim’s network with multiple UDP packets.
If you are curious to know how to perform a DDoS attack and bring down any website, keep reading this article as in this article, a step-by-step method is given to perform a DDoS attack using the command prompt (CMD).
Бо истифода аз CMD чӣ гуна ҳамлаи DDoS-ро дар вебсайт анҷом додан мумкин аст
To perform a DDoS attack on a website using the command prompt (CMD), follow these steps:
Шарҳ: In order to perform this attack, you should have a good internet connection with unlimited bandwidth.
1. Select the website on which you want to perform the DDoS attack.
2. Find the IP address of that website by following these steps.
a. Open the command prompt.
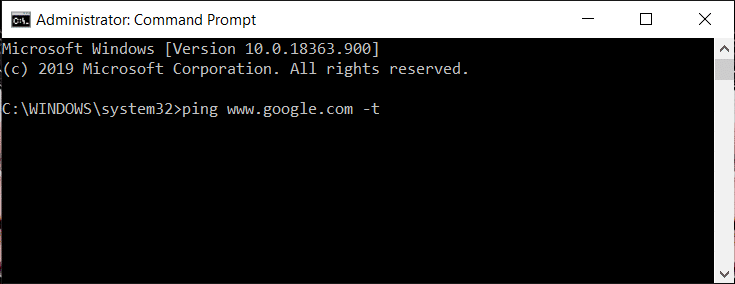
b. Enter the below command and hit the enter key.
ping www.google.com –t
Шарҳ: Replace www.google.com with the website on which you want to perform the DDoS attack.
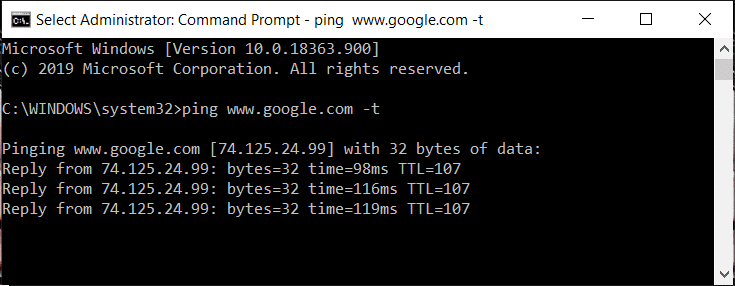
c. You will see the IP address of the selected website in the result.
Шарҳ: IP address will look like: xxx.xxx.xxx.xxx
3. After getting the IP address, type the below command in the command prompt.
ping [ip address of selected website] –t –l 65500
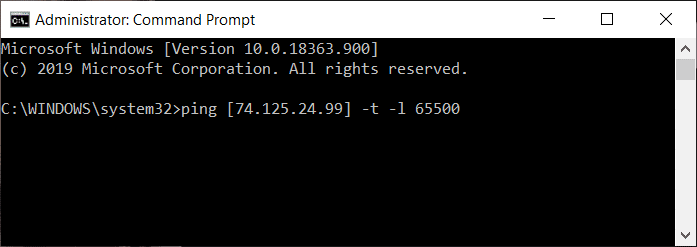
Using the above command, the victim computer will be pinged with infinite data packets of 65500.
Дар фармони боло:
- Дар пинг sends the data packets to the victim website.
- The IP address of the selected website is the IP address of the victim website
- Дар -t means that the data packets should be sent until the program stops.
- Дар -l specifies the data load that is to be sent to the victim website.
- Арзиш 65500 is the number of data packets that have been sent to the victim website.
4. Hit the enter button to run the command and make sure to run the command for hours.
Шарҳ: In order to make the attack more effective, you should perform an attack on the victim’s website with pings from more than one computer. To do so, just run the same above command on the multiple computers at the same time.
5. Now, visit the website after 2 or 3 hours. You will notice that the website is temporarily down or the server is displaying the дастрас нест message there.
So, by following each step carefully, you will be able to perform a successful DDoS attack on a website using just Command Prompt to bring it down or temporarily crash it.
You can also see the effect of the DDoS attack on the targeted website using the менеҷери вазифаи and by viewing the network activities.
To see the effect of the DDoS attack on the targeted website, follow these steps.
1. Кушодани менеҷери вазифаи дар компютер.
2. Right-click and select Start task manager.
3. You will notice six tabs under the menu bar. Click on the Networking
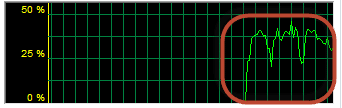
4. You will see the results similar to the results shown in the figure below.
Ҳамчунин хонед: Чӣ тавр насб кардани Linux Bash Shell дар Windows 10
The conclusion is that if the DDoS attack on the targeted website is successful, you will be able to see the increased network activities which you can easily verify from the networking tab of the task manager.